See this product in action
Paxton10 – Single-door controller, PoE
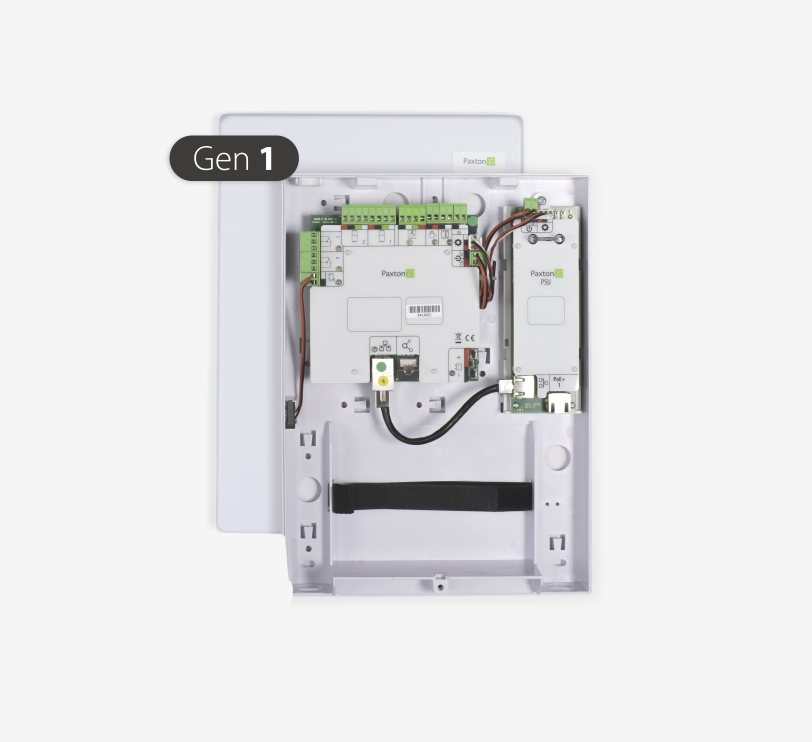
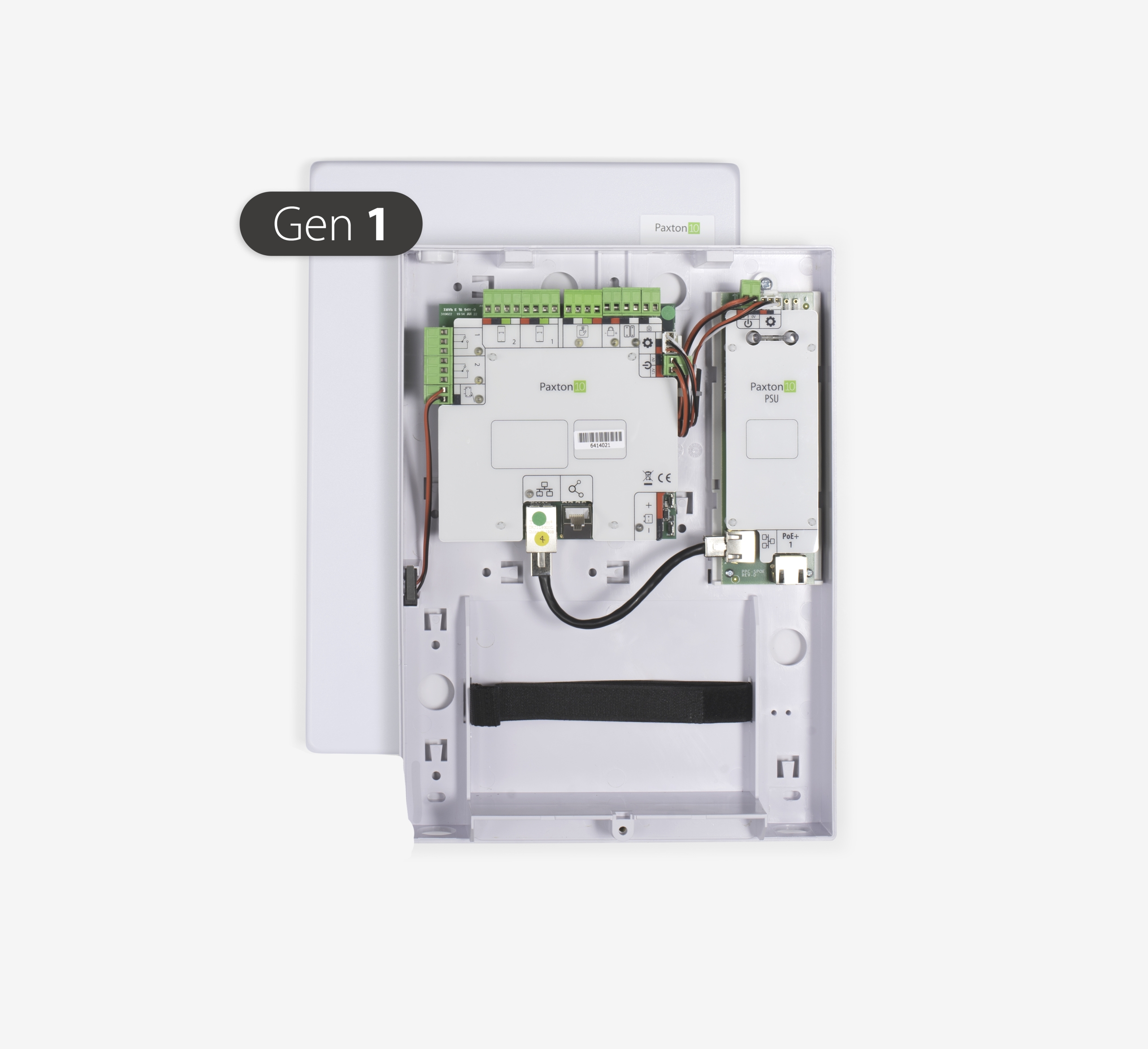
About Paxton10 Door Controllers are the building blocks of the Paxton10 system. Each one provides control of a single door and a port to allow support for up to three Paxton10 Wireless Connectors for additional functionality. A single Paxton10 system can include up to 1000 door controllers.
The Paxton10 door controller is a network device that communicates over TCP/IP and can be integrated into an existing network infrastructure.
PoE+ – The Paxton10 PoE+ Door Controller includes a built-in PoE+ splitter, allowing both the controller and door lock to be powered via PoE+. This eliminates the need for a 230V connection at the door. We recommend using a PoE+-enabled TCP/IP network switch.
The door controller is equipped with 4 inputs, tamper, 230v fail, door contact and RTE.
An intruder alarm can be integrated using the Paxton10 alarm connector.
Please note: If an independent backup battery is required for the 2nd generation controller, the site infrastructure must have a UPS.
Power – Mains powered and PCB only (with or without plastic enclosure) options also available.
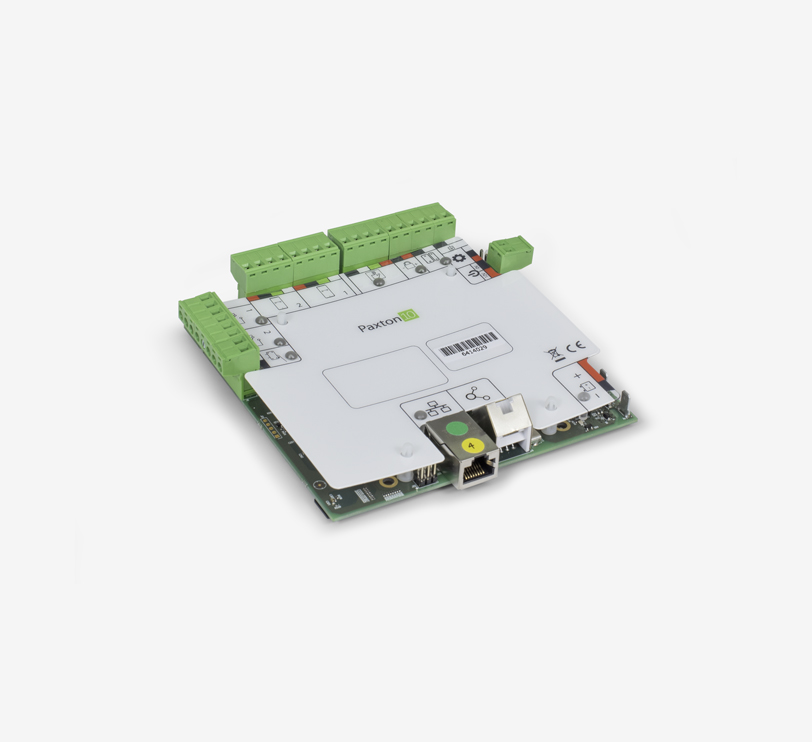
Installation – The wiring label on the Paxton10 Door Controller clearly shows colour-coded connections for the readers, power supply, lock, etc. The 12v output for the lock can be used to control any door, barrier or gate. Diagnostic LEDs indicate the status of the controller and its inputs and outputs.
Controllers are connected directly to the network via TCP/IP. They are automatically visible in the Paxton10 software under the devices menu.
Operation – Any changes made in the Paxton10 software are immediately communicated to the door controller. When a user presents their token to the reader, the control unit identifies them and permits or denies access as appropriate.
Complete your system
Other products you might be interested in…